How email hacking works?
Email hacking is the unauthorized access to an email account or email correspondence. There are a number of ways in which a hacker can illegally gain access to an email account, and the majority of them rely on the behaviour of the account’s user. Our datacenters use a variety of softwares and firewall at server level but the best tools are not valuable if customers do not practice our safety tips and protect their computers and other devices that are used to correspond.
The most common methods to hack an email account are as follows.
– Phishing Attack
– Malware Attack
Phishing Attack is the most widely used hacking technique in which hacker usually sends an e-mail that appears to come from a bank, or credit card company or ISP — requesting “verification” of information. Usually emails also claims that you have exceeded the storage limit for your mailbox and, therefore, your email account will be closed if you do not click a link to increase your storage capacity. These messages ask for verification of personal information, such as an account number, a password, or a date of birth. Twenty percent of unsuspecting victims respond, which may result in stolen accounts, financial loss, or even identity theft. It is best not to respond to unsolicited emails as they may be attacks of this kind.
Malware Attack, or “malicious software,” is designed to secretly access your computer, compromise email accounts and steal data. Malware can be introduced into a computer while browsing the internet or opening an email. To spread Malware, hackers can create malicious websites of their own, exploit a vulnerability in the applications a website relies on. Malware is often downloaded from an email attachment asking to open attached document e.g. Export Documents, Quotation request, Inquiry, PO Order. We strongly advise you to install latest malware scanners on your machine and keep automatic updates enabled in order to protect yourself from email hacking.
Live Demonstration of Phishing Attack:
Here is the sample of Phishing attack through an email to hack email password and snatch the money.
Screenshot #1 – You receive an email from hacker on your own domain to verify your account.
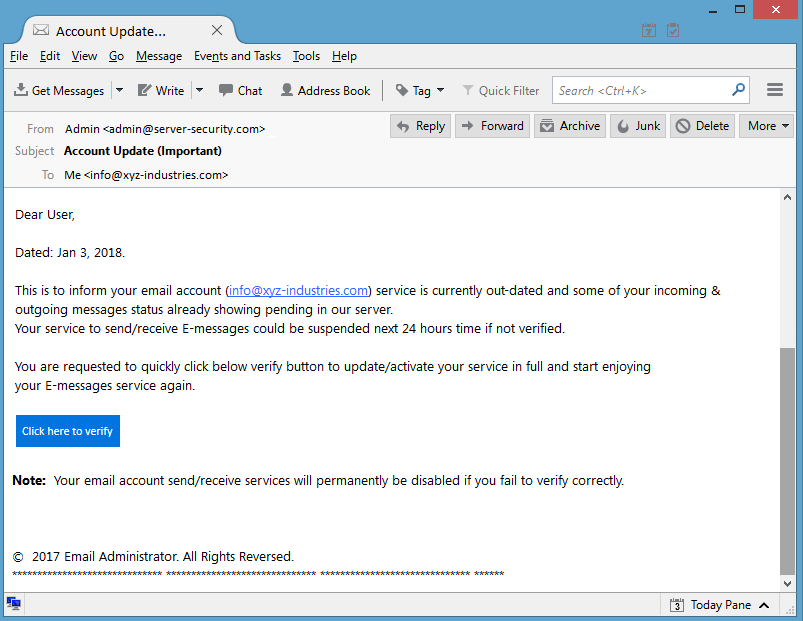
Screenshot #2 – If you press the blue button “Click here to verify” from above screenshot, next window will ask to provide your account information.
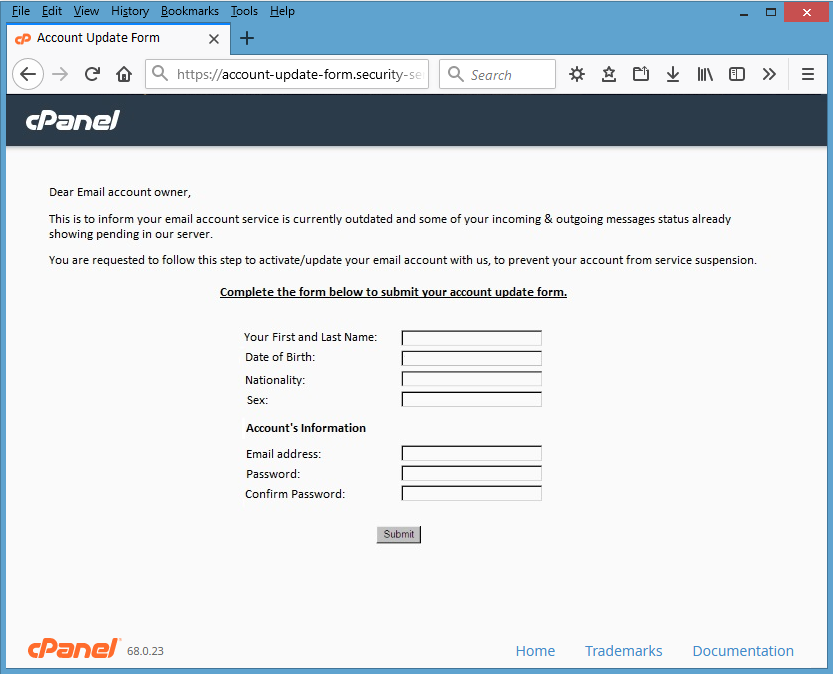
Screenshot #3 – When you fill the above form, hacker will get your email password and will login into your webmail to forwarders and filters as follows.

Screenshot #4 – After successful login, hacker clicks on your email address as follows.

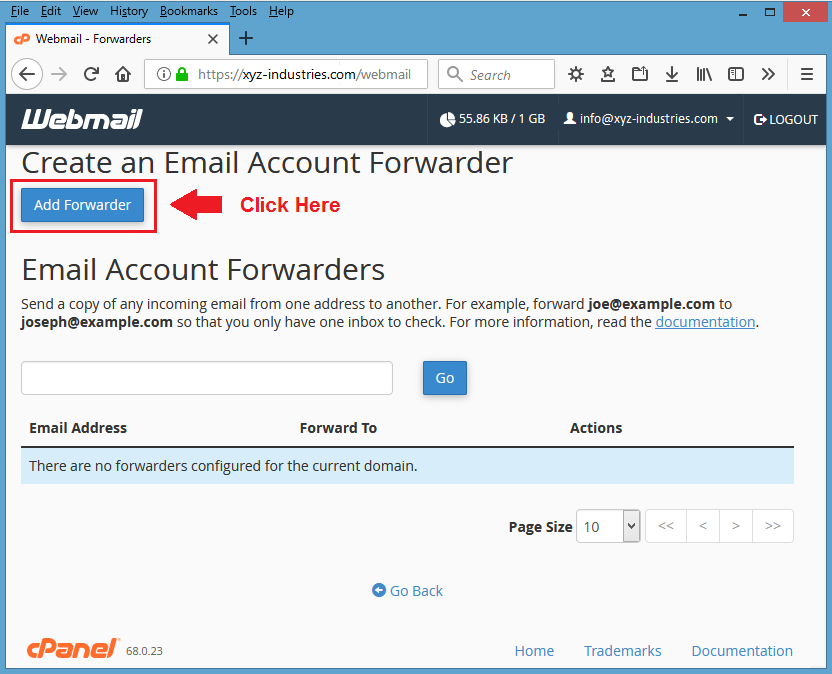
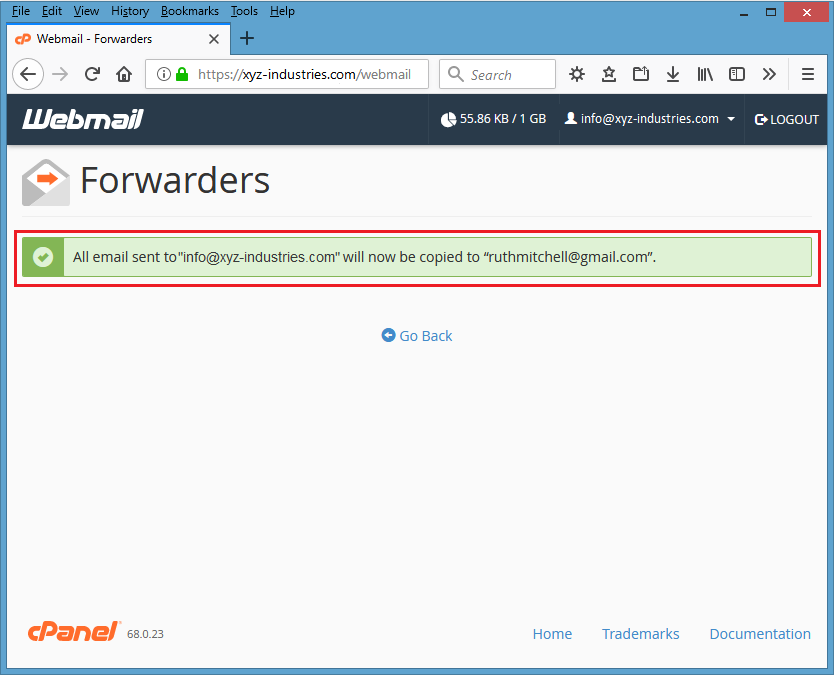
Screenshot #5 – Hacker clicks on “Forwarders” to get the copy of your each email message on his own separate email address.

Screenshot #6 – Hacker clicks the button “Add Forwarder”
Screenshot #7 – Hacker places his own email address in “Forward to Email Address” box, and press “Add Forwarder” button.
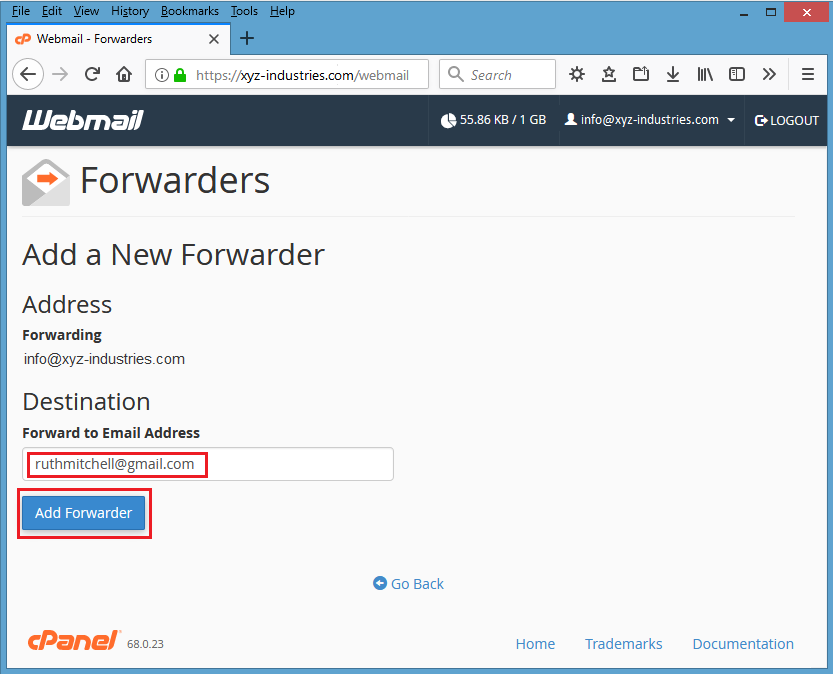
Screenshot #8 – Here is the confirmation of forwarder’s settings.
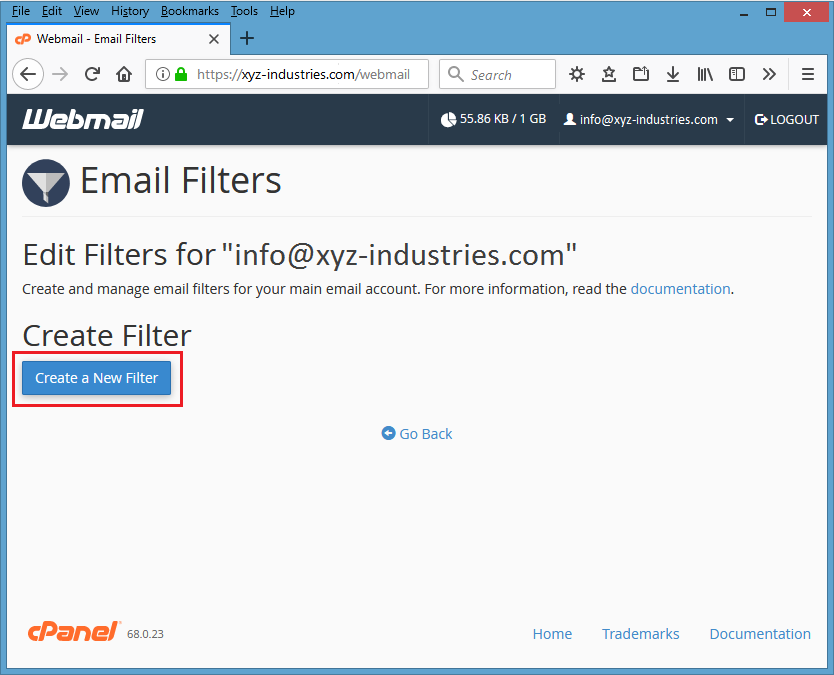
Screenshot #9 – Hacker now clicks on “Email Filters” option to divert emails of those customers which are about to send you the payment.

Screenshot #10 – Hacker clicks the button “Create a New Filter” to create new filter.
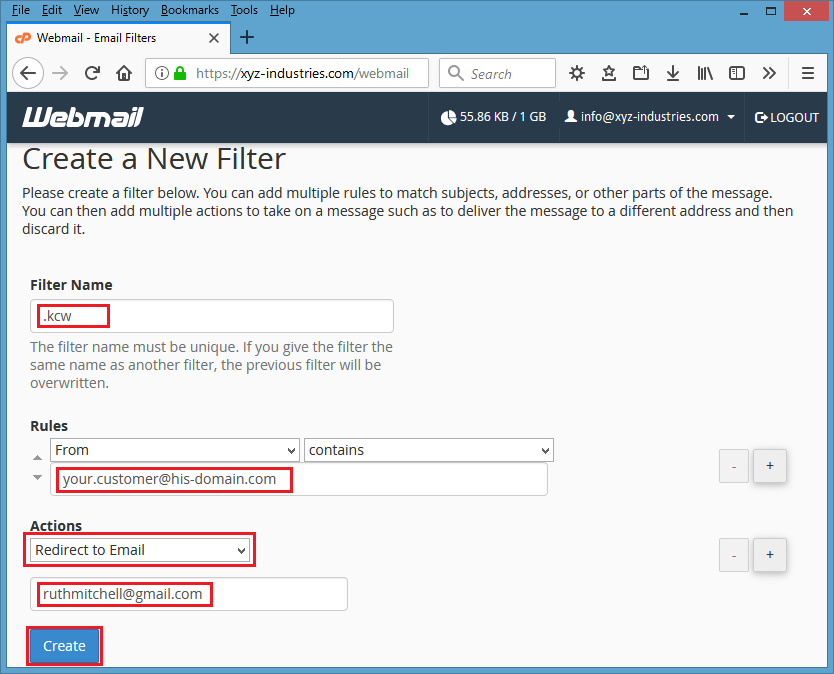
Screenshot #11 – Hacker places his own email address to divert emails of any particular customer. This way you will not receive any email from your customer and hacker will communicate on your behalf to transfer away the money somewhere else.
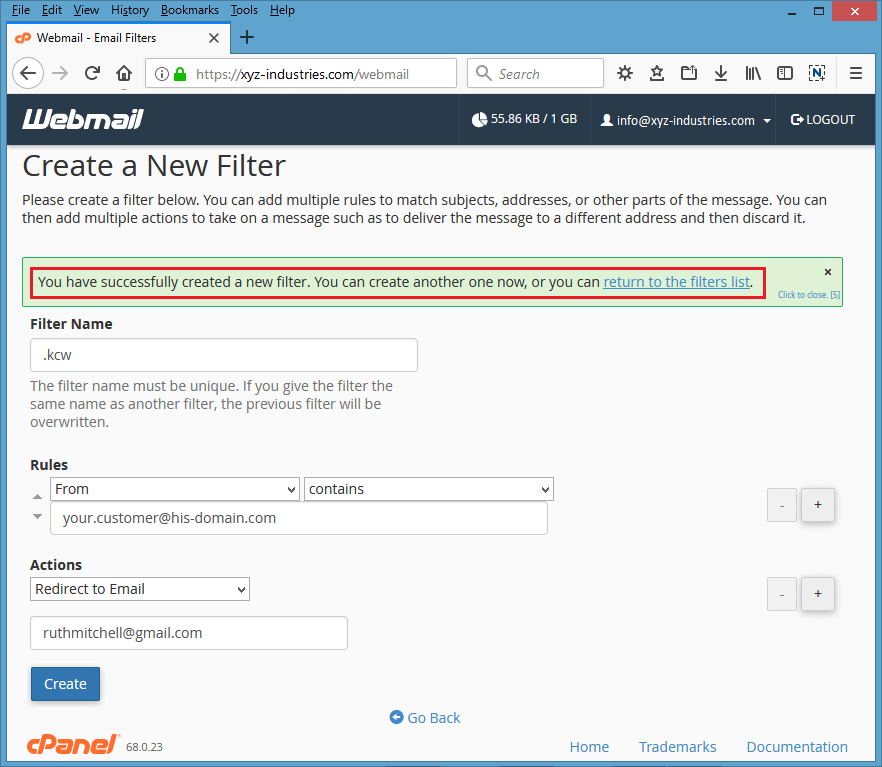
Screenshot #12 – Here is confirmation of filter’s creation.
Tips:
Here are some useful tips that can help you to secure from Email Hacking.
1- Change your password
2- Enable two-factor authentication
3- Scan your computer for malware
4- Check your email settings

